Our Approach to Security
The policies, protocols, and protections we have in place were developed with one goal: to safeguard the privacy and security of your intranet, your firm, and your data.
SOC 2 Compliant
Knowledge Architecture is SOC 2 Type 2 compliant and performs annual SOC 2 Type 2 audits.
GDPR Compliant
Knowledge Architecture is compliant with the EU’s General Data Protection Regulation.
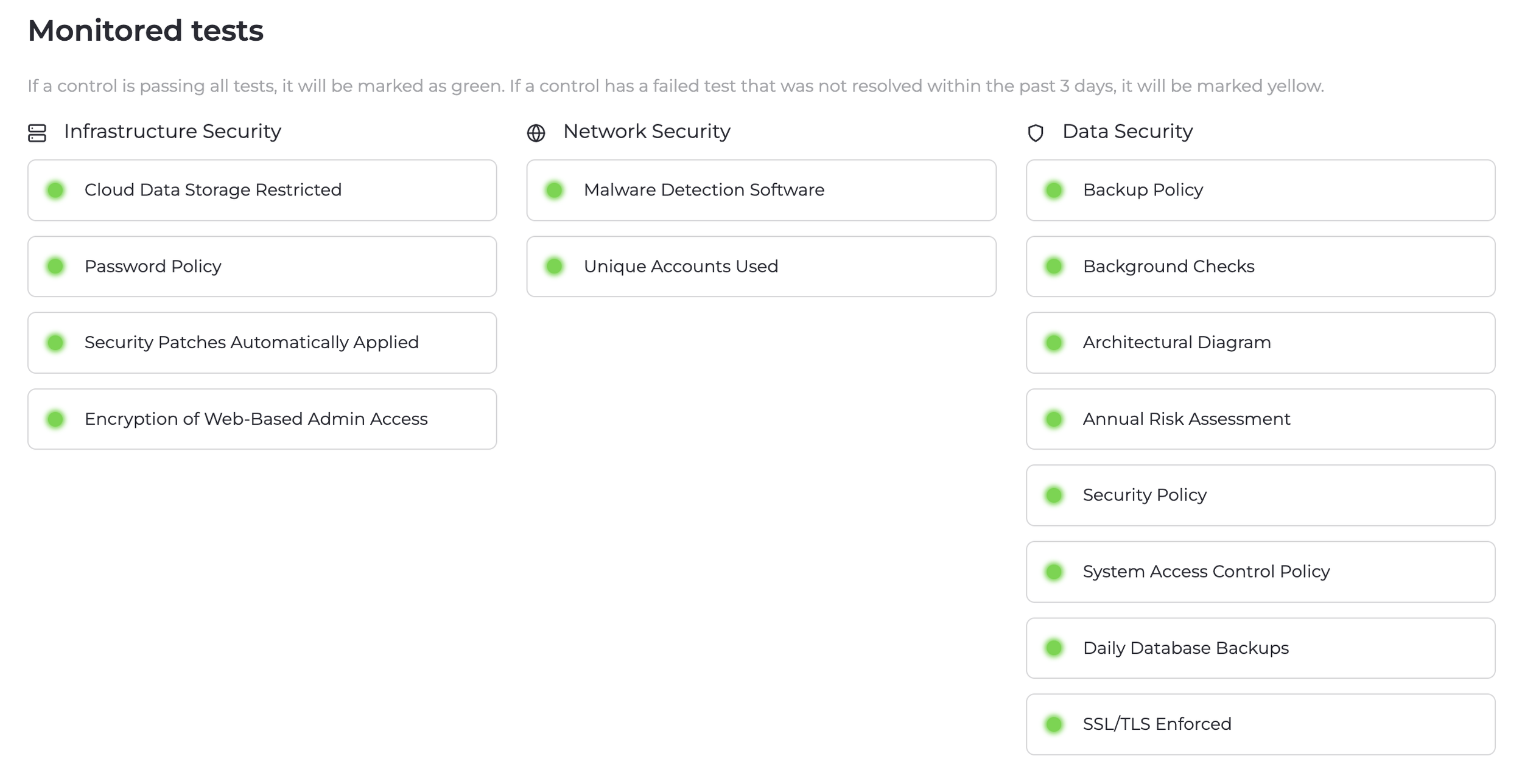
Visit our Trust Center
Our Trust Center, powered by Drata, provides real-time transparency into our security posture and the opportunity to review our SOC2 Attestation, Penetration Test Report, and Security Policies.
Physical Security
All customer data resides entirely in our Azure production environment, physically located within multiple Azure data centers to provide better redundancy and performance.
Physical protections are entirely provided by Azure, which have a wide range of security certifications and attestations to its physical security including SOC2 and ISO 27001. Learn more about Azure data center security. No data or production systems are located outside of an Azure data center.
Identity Management and Access Controls
Synthesis 6 leverages Azure AD as our Identity Provider, using the OpenID Connect standard. As a result you are able to use all features contained within Azure AD, such as Session Duration, Two-Factor Authentication, and User and Group Provisioning via SCIM (System for Cross-domain Identity Management).
Knowledge Architecture will never possess, or have access to, your employees’ credentials.
User Access logging and auditing can be accessed and managed through your Azure AD portal.
Cloud and Data Security
Knowledge Architecture performs network security and server hardening, administrative access control, system monitoring, logging and alerting, and other industry standard best practices.
Knowledge Architecture leverages the Microsoft Defender for Cloud tool to maintain a constant security posture assessment, perform vulnerability scanning, alert for suspicious behaviors, and prevent any deviation from a specified allowed configuration.
Knowledge Architecture encrypts data at rest and data in transit for all of our customers.
All data transmitted between Synthesis 6 infrastructure and client browsers is secured using strong encryption protocols via HTTPS. Synthesis 6 supports the latest recommended secure cipher suites to encrypt all traffic in transit, including use of TLS 1.2.
Data at rest is encrypted and protected by secure 256-bit AES encryption.
Database backups are also encrypted at rest and while in transit.
Data Processing Addendum
We provide a standard Data Processing Addendum (DPA) to demonstrate how we comply with obligations imposed on Data Processors handling Personal Data for Data Controllers.
Subprocessors List
Knowledge Architecture uses subprocessors to provide our services. We enter into data processing agreements as required by law with each of them.
Security Questions?
Send us an email | 415.523.0410